Here is a simple switch to verify the state of an Exchange database. To check the header of the log file you can use the following command:. Right-click on it and select Properties Click on the Security tab and then tick the following checkboxes: Check the quick solution: The more memory inside the Exchange Server, the more information can be kept in memory. In the command prompt, perform the Hard recovery from the BIN folder with the following command:. Naturally you would need to substitute "name of temp folder" for a real folder. 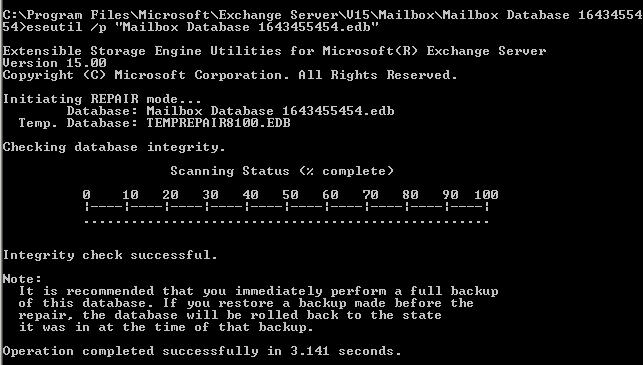
| Uploader: | Tukus |
| Date Added: | 17 August 2010 |
| File Size: | 7.69 Mb |
| Operating Systems: | Windows NT/2000/XP/2003/2003/7/8/10 MacOS 10/X |
| Downloads: | 93206 |
| Price: | Free* [*Free Regsitration Required] |
Fixed: Exchange 2010 ESEUtil Failed with Jet Error 1032
This Information Store Integrity Checker can repair the database at the application level. In the header information you 0210 see the Log File Signature: When the page is saved into the database file, the checkpoint file is updated.
Syslog messages contain useful information for troubleshooting network problems. Recently, my edb file got corrupt due to dirty system shutdown, so I tried to repair using Eseutil but got no success.
It can also detect when services have stopped, or if there is a network latency problem.
Having alerted you to the dangers, I want to emphasise that there will be circumstances where eseutil is a life-saver. Here, eseutul look at identifying a checksum error, understanding health of an Exchange database and how to know which log file belong to which database.
Every Database file, log file and checkpoint file have a header. This special file Restore. You need to recover a store.
Eseutil Exchange 2010
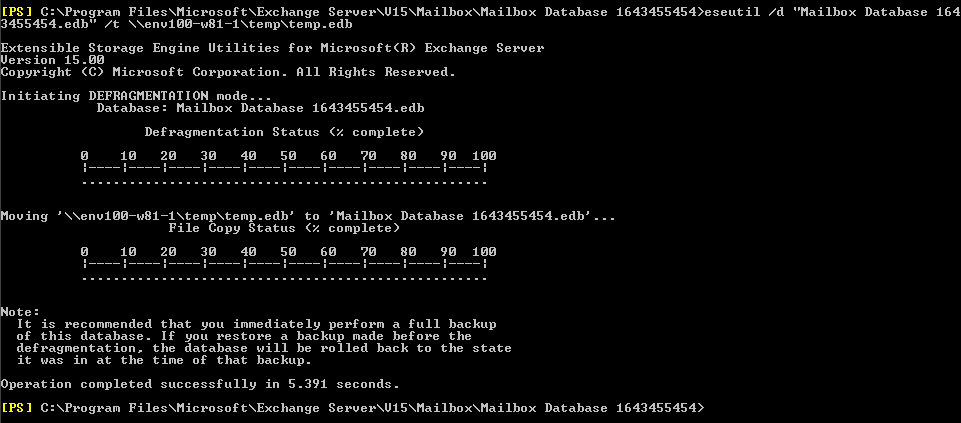
Soft Recovery Soft recovery replays the logs — eseytil only those after the last checkpoint. Look at our blogs, We have explained it clearly step by step. You would like to recover the space occupied by the deleted mailboxes. An operation is first processed into the memory and then dissevered into pages. You must have Javascript enabled in your Browser in order to submit a comment on this site.
Here I have tried to explain the terminologies involved in a repair process like how the Exchange JET database stores information properly arranged in physical and logical pages eweutil how the repair, defrag and ISINTEG process get rid of corruption.
Microsoft Exchange Eseutil Commands mh | Examine Databases Files
Secondly, this tool can be used along with other eseutil switches easily with the help of space between them. If a the Mailbox database is dismounted or stopped, then the logs pile up. If the backup was taken a few days back and there were logs created in the production location once the backup was done, then we must make sure that the production location contains the sequence of logs from the one in the restore.
Specialist use only, I find the output fascinating but not very useful. In the database header you can find all information regarding this particular database; like the date it was created in the database signatureif it was switched off properly dirty shutdown versus clean shutdownthe accompanying log file signature and for example when the last full and incremental backup was created unfortunately not visible in the screenshot. An old trick is to copy the Address as seen in Explorer and then go to the command prompt, right-click and paste that path.
This command will read all log files and show immediately if they are in the same sequence, if the sequence is complete and if all log files are ok.
Where the f drive has enough free space. Exchange Database Recovery — Using eseutil commands The real job of an exchange administrator is to maintain high availability when it comes to a messaging environment. But there are many misconceptions about using these utilities. A highly corrupted Exchange database will lead to the loss of data. Learn about the latest security threats, system optimization tricks, and the hottest new technologies in the industry. To check the header information of the checkpoint file you can use the following command:.
Likely contents of restore. Jaap Wesselius Posted On June 4, In 90 percent of the cases, this problem is resolved automatically, and for rest 10 percent, there is ESEutil for help.

This header contains internal information used by Exchange. As soon as a transaction is created in memory it is immediately written from memory to the log file in use, which is E This is because you will want to be safe and replay all the transaction logs.
Suspect missing log files.

Comments
Post a Comment